ACCESS CONTROL SYSTEMS
IMAporter Pro
Robust access control system suitable for large and medium-sized companies. It can do everything that the lower IMAporter series of access control systems can, but in addition, thanks to its huge variability and many modules, the system can be tailored to suit the needs of even the most demanding clients.
Unlimited number of entry points
Compatible with OtevírejMobilem (Mobile Access Platform) app
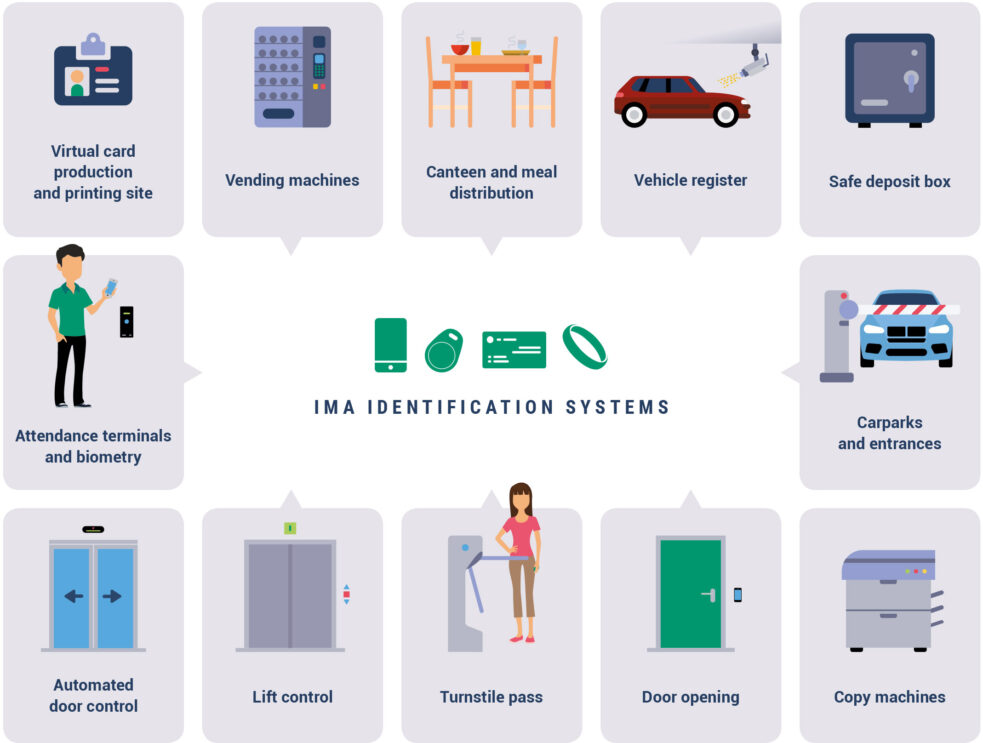
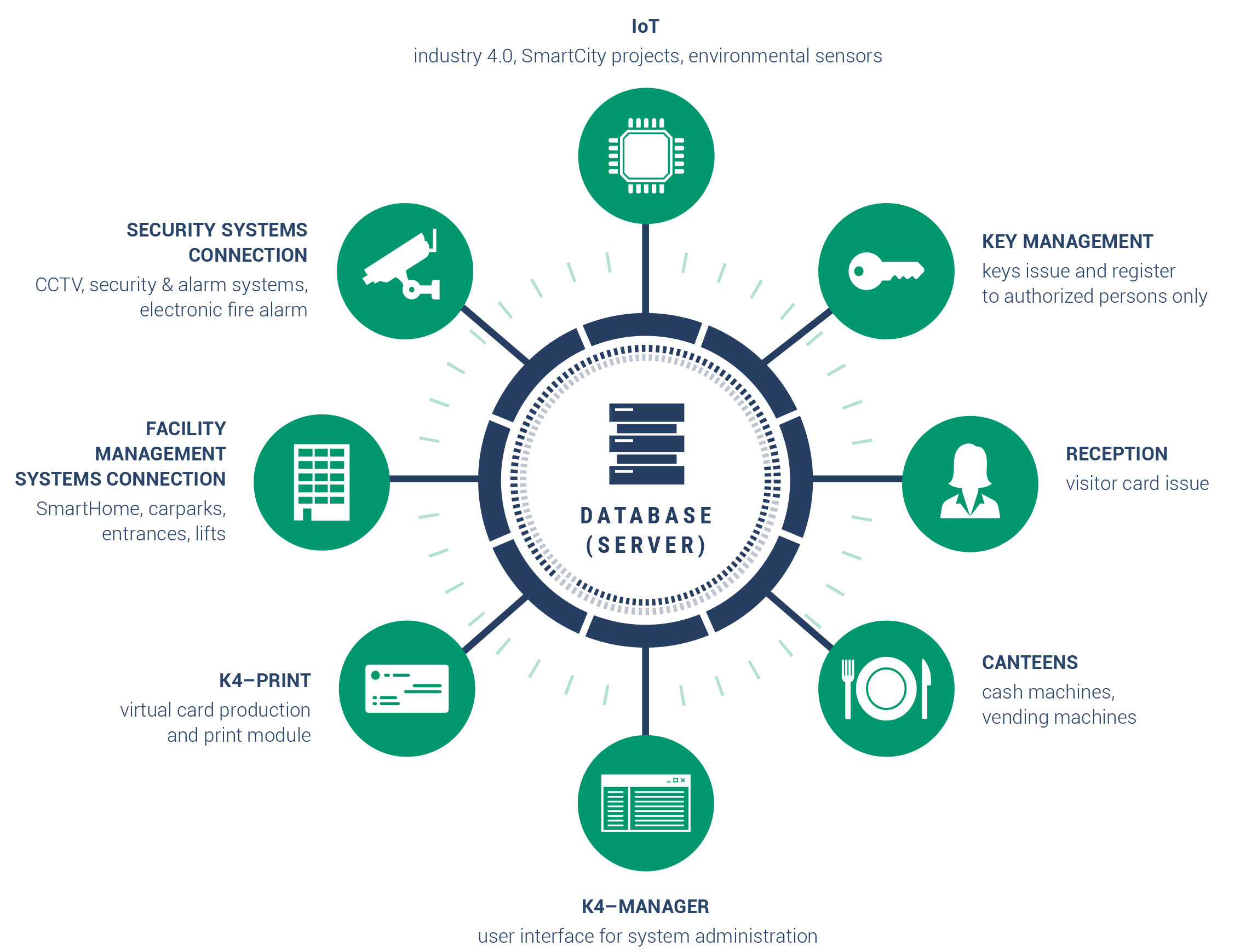
Connectivity to other systems, more than 50 modules
System is managed by your security or IT department via desktop app